Requirements
- SSO is only supported for workspaces on the Business plan. Visit the Pipedream pricing page to upgrade.
- You must be an administrator of your Pipedream workspace
- You must have an Okta account
Configuration
Visit your Okta dashboard
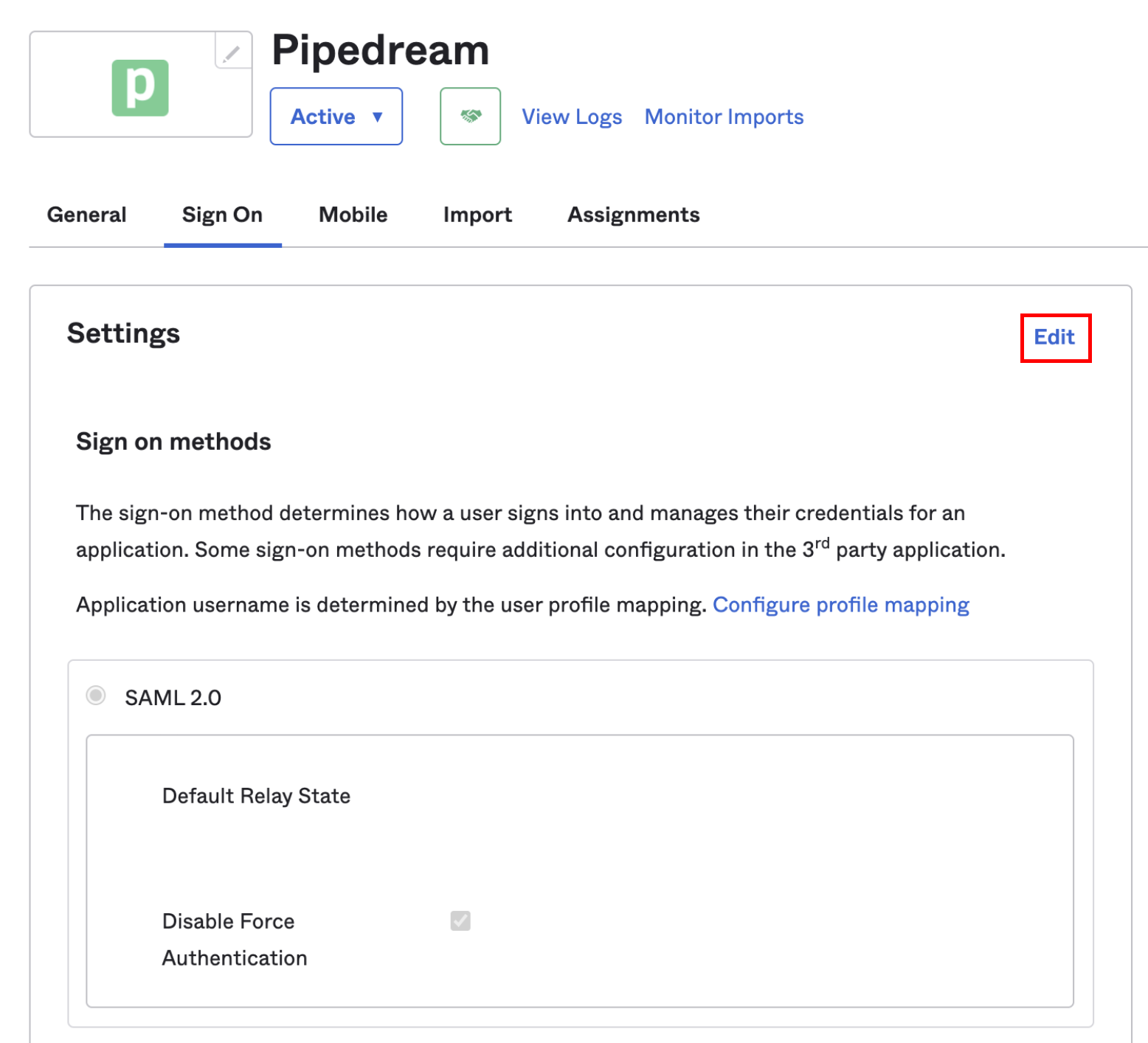
In your Okta Admin dashboard, select the Applications section and click Applications below that: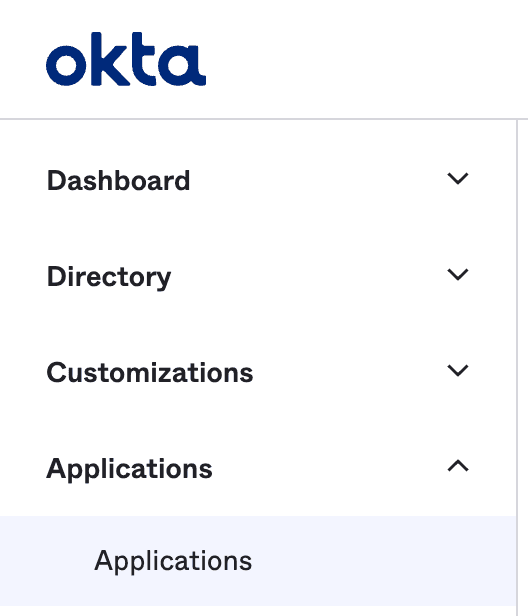

Configure Default Relay State
Scroll down to the SAML 2.0 settings. In the Default Relay State section, enter 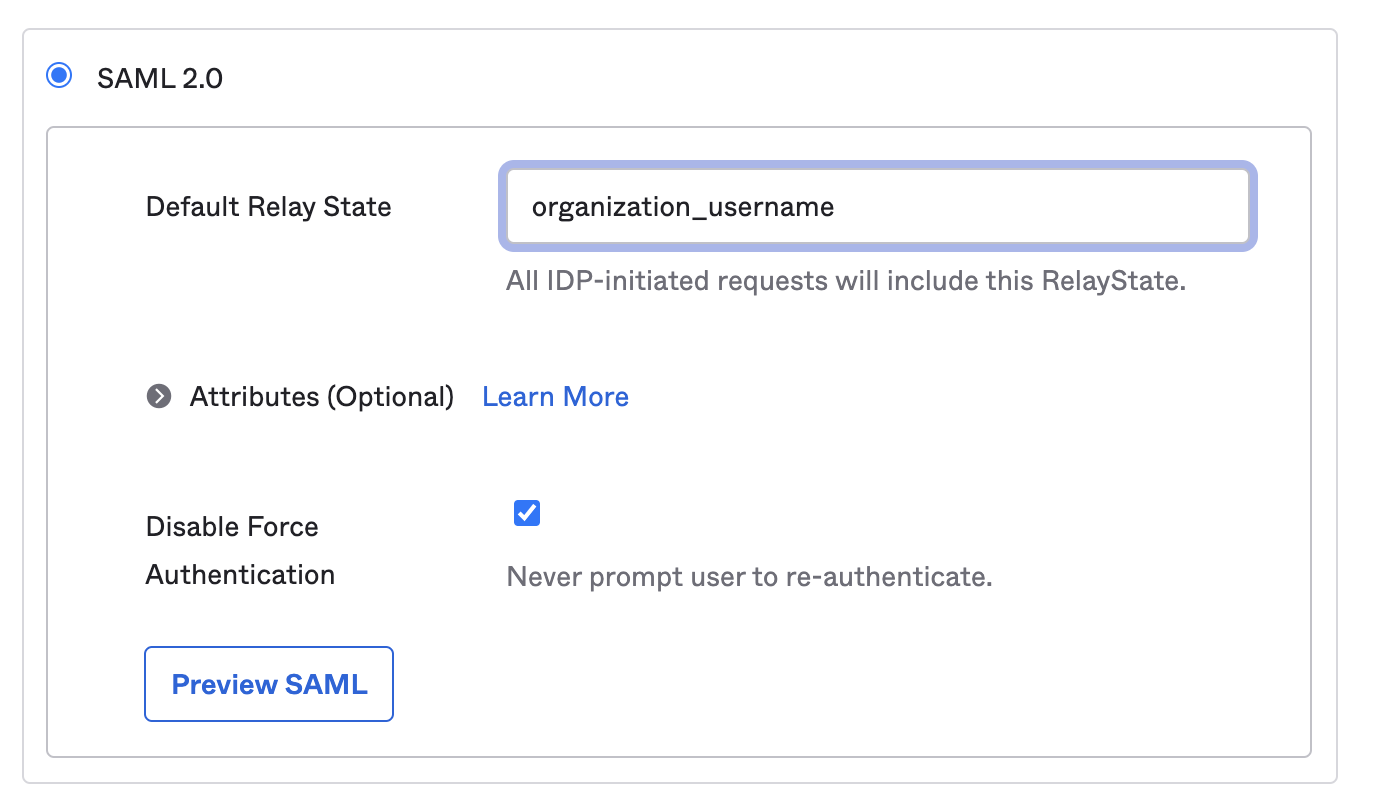
organization_username:
Save your configuration
Set any other configuration options you need in that section or in the Credentials Details section, and click Save.
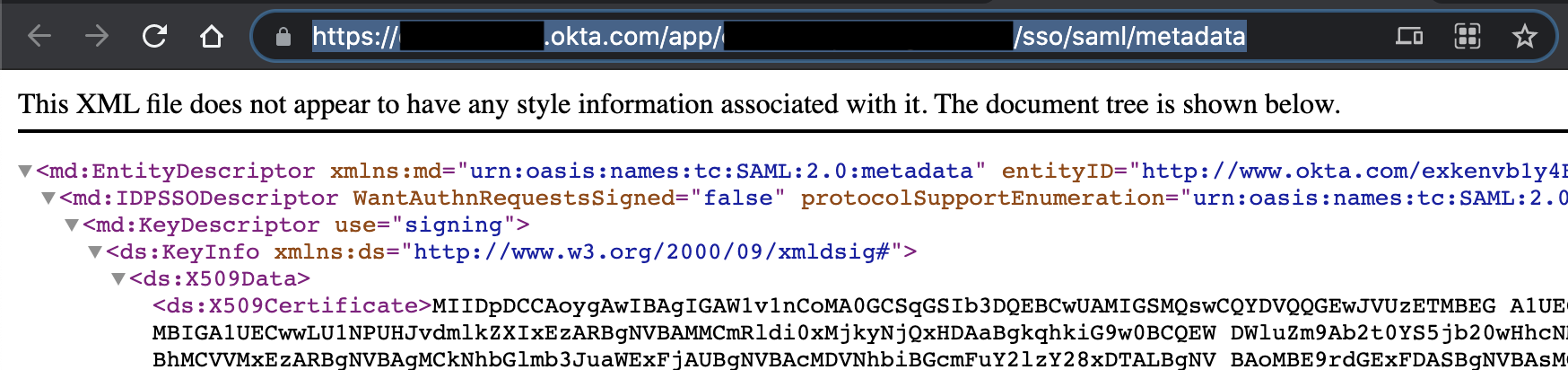
Copy the Identity Provider metadata URL
In the Sign On section, you’ll see a section that includes the setup instructions for SAML: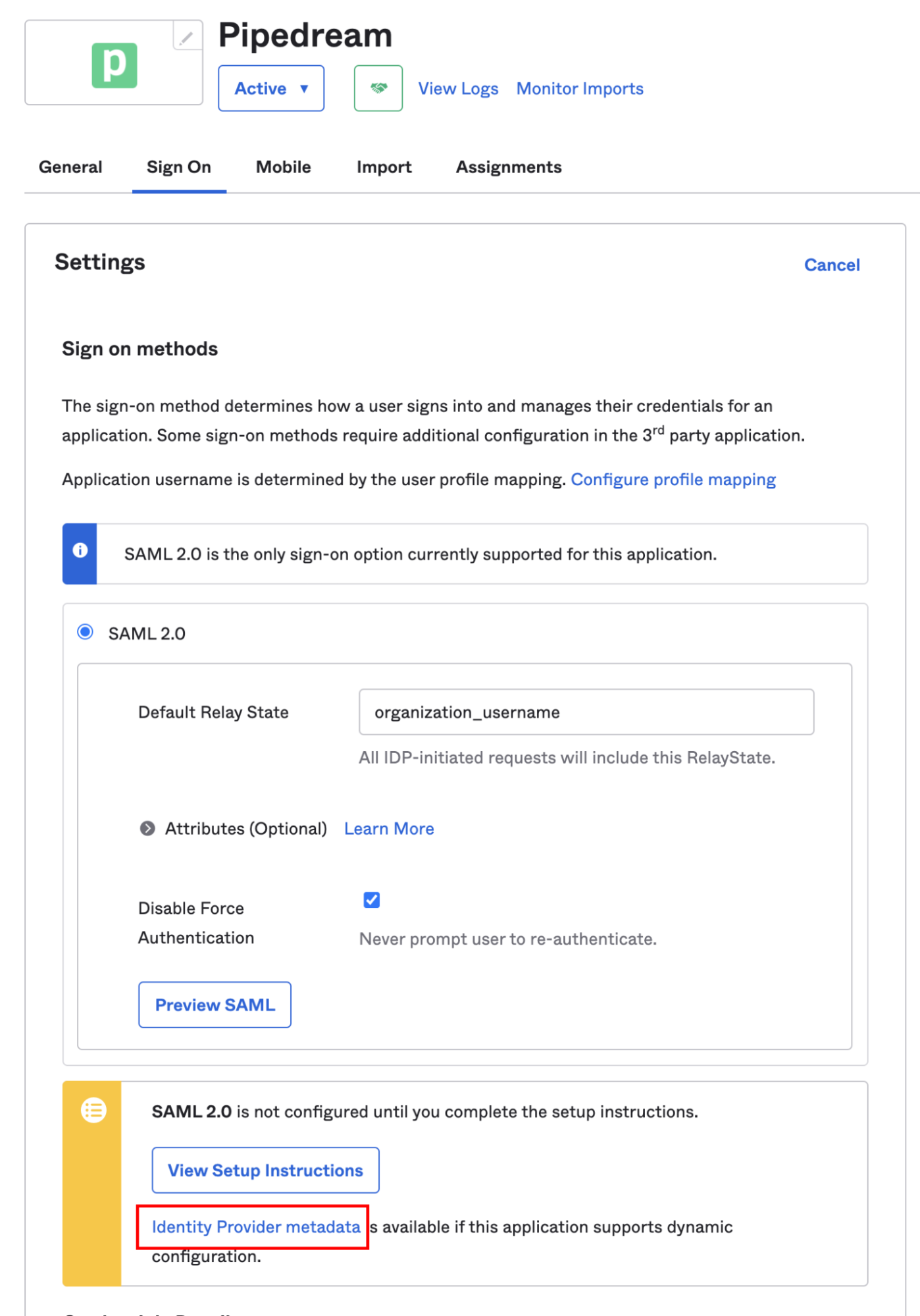


Enable SSO in Pipedream
Visit your Pipedream workspace authentication settings. Click the toggle to Enable SSO, then click Edit SSO Configuration, and add the metadata URL in the SAML section and click Save: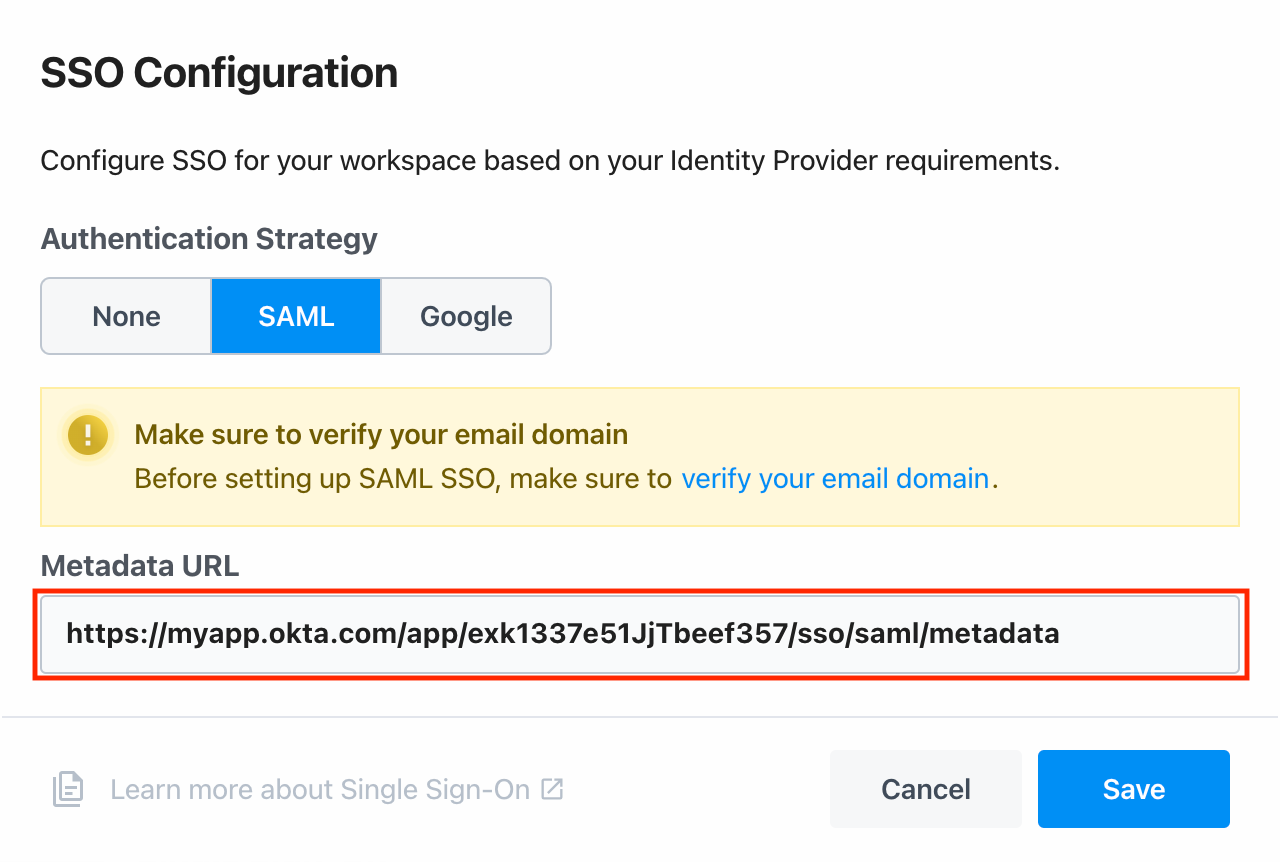

your-workspace-name is the name of your workspace.