Add the workflow's endpoint URL to your report-uri or report-to directives in your CSP. This saves the data to a table in the SQL service and sends formatted violation data to Slack.
How this works
This workflow saves Content-Security Policy violations to a table in the Pipedream SQL service for analysis, and sends a formatted message about the violation to Slack.
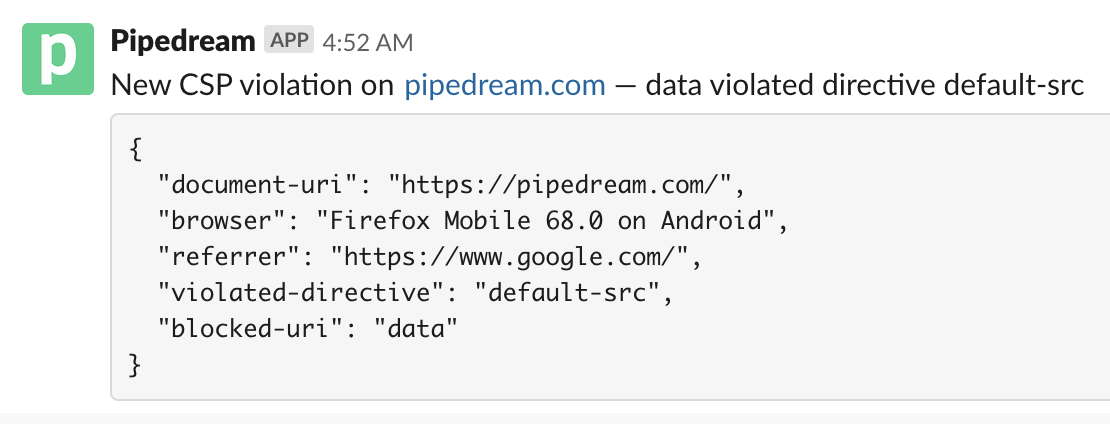
If you want to run analysis on CSP violation data (see the SQL section below), or send yourself notifications of violations (via Slack, Discord, etc.), you're in the right place!
Quickstart
Just add the workflow's HTTP endpoint as the report-uri directive of your CSP. Here's how:
Copy this workflow. This will generate a URL specific to your copy of the workflow, at the top of the workflow, under the HTTP trigger step. This URL can accept any HTTP request. We'll use that URL in step 3.
In the send_slack_message step, press the Connect Account button to link your Slack account, and enter the Slack channel where you'd like to send notifications. See the Modifying the workflow section if you'd like to send these notifications somewhere else.
Copy the workflow's HTTP endpoint and add it to your Content-Security Policy's
report-uridirective:
Content-Security-Policy:
report-uri https://yourendpoint.m.pipedream.net
Once you deploy this change, you should start receiving new CSP violations as HTTP requests in your workflow. You can examine each violation from the Inspector on the left, examining its full data along with the workflow's execution logs.
Modifying the workflow
By default, this workflow sends formatted messages about CSP violations to Slack. You can remove this step and send yourself an email, or send messages to Discord
If you'd prefer to send the violation JSON to your own data store, you can swap out that step, too.
In general, you can modify this workflow however you'd like: you can run any Node code, require any npm package, and more.
Querying the data with SQL
Visit the SQL UI and run a query like this to explore the data:
SELECT *
FROM csp_violation_data
LIMIT 10;
Each section of the violation report will be included in its own field, so you can select or group by them to ask interesting questions. For example, let's rank the count of reports by directive and URL to see the top issues contributing to violations:
SELECT effective_directive, blocked_uri, COUNT(*)
FROM csp_violation_data
GROUP BY 1, 2
ORDER BY 3 DESC;
The SQL service uses Presto. You can learn more about running queries and the Presto SQL dialect in the Pipedream docs